
OpenVPN 是一个开源的虚拟私人网络(VPN)实现软件,它可以用来建立安全的点对点或站点到站点连接。通过使用 OpenVPN,用户可以在不安全的网络上建立加密连接,确保数据传输的安全性和隐私性。
操作系统:CentOS-7.x
一、准备篇
1、关闭selinux
#执行以下命令
setenforce 0
sed -i 's/^SELINUX=.*/SELINUX=disabled/' /etc/selinux/config
2、防火墙设置
关闭firewall
systemctl stop firewalld.service #停止firewall
systemctl disable firewalld.service #禁止firewall开机启动
systemctl mask firewalld
systemctl stop firewalld
yum -y remove firewalld
安装iptables防火墙,开启tcp 1194端口
yum -y install iptables-services #安装
vi /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
:wq! #保存退出
systemctl enable iptables.service #设置防火墙开机启动
systemctl restart iptables.service #启动防火墙使配置生效
3、设置系统时间
rm -rf /etc/localtime #先删除默认的时区设置
ln -s /usr/share/zoneinfo/Asia/Shanghai /etc/localtime #替换亚洲/上海作为默认时区
vi /etc/sysconfig/clock #添加时区
Zone=Asia/Shanghai
:wq! #保存退出
timedatectl set-local-rtc 0
hwclock --systohc -u #系统时钟和硬件时钟同步,当前系统时区不为 UTC,是CST时间,所有要加-u参数
date #显示系统时间
date -s "2024-03-13 15:24:00" #修改时间
watch -n 1 date #显示实时时间
yum install ntp
ntpdate ntp.aliyun.com #同步时间服务器
echo -e "0 0 * * * /usr/sbin/ntpdate ntp.aliyun.com &>/dev/null" >> /var/spool/cron/root #添加计划任务
systemctl restart crond.service #重启服务
4、开启内核转发
vi /etc/sysctl.conf
net.ipv4.ip_forward = 1
sysctl -p #立即生效
5、系统参数优化
vi /etc/security/limits.conf #在最后一行添加以下代码
* soft nproc unlimited
* hard nproc unlimited
* soft nofile 1000000
* hard nofile 1000000
:wq! #保存退出
vi /etc/sysctl.conf #在最后一行添加以下代码
fs.file-max = 65535000
fs.nr_open = 65535000
kernel.pid_max=655350
vm.swappiness = 0
:wq! #保存退出
/sbin/sysctl -p
ulimit -a #查看
ulimit -n 1000000 #设置
6、安装依赖包
yum install openssl-devel lzo-devel pam-devel gcc
7、安装包下载
https://www.rpmfind.net/linux/epel/7/x86_64/Packages/o/openvpn-2.4.12-1.el7.x86_64.rpm #openvpn安装包
https://www.rpmfind.net/linux/epel/7/x86_64/Packages/p/pkcs11-helper-1.11-3.el7.x86_64.rpm #安装openvpn需要的依赖包
https://github.com/OpenVPN/easy-rsa/releases/download/v3.0.8/EasyRSA-3.0.8.tgz #用来制作证书的工具
上传安装包到/data/soft目录
二、安装篇
1、安装openvpn
cd /data/soft
rpm -ivh pkcs11-helper-1.11-3.el7.x86_64.rpm
yum localinstall openvpn-2.4.12-1.el7.x86_64.rpm
yum list installed openvpn
注:安装完成后,会自动创建用户openvpn、用户组openvpn
2、制作证书
cd /data/soft
tar xfz EasyRSA-3.0.8.tgz -C /etc/openvpn/
mv /etc/openvpn/EasyRSA-3.0.8 /etc/openvpn/EasyRSA
chown -R root:root /etc/openvpn/EasyRSA -R
chmod 755 /etc/openvpn/EasyRSA -R
cp /etc/openvpn/EasyRSA/vars.example /etc/openvpn/EasyRSA/vars
vi /etc/openvpn/EasyRSA/vars #修改下面的信息,也可以不改,不影响使用
set_var EASYRSA_REQ_COUNTRY "CN"
set_var EASYRSA_REQ_PROVINCE "ShannXi"
set_var EASYRSA_REQ_CITY "Xian"
set_var EASYRSA_REQ_ORG "Ltd."
set_var EASYRSA_REQ_EMAIL "xx@xx.com"
set_var EASYRSA_REQ_OU "OpenVPN"
:wq! #保存退出
cd /etc/openvpn/EasyRSA
./easyrsa init-pki #初始化,在当前目录创建pki目录
./easyrsa --batch build-ca nopass #创建CA证书,不需要密码
./easyrsa gen-dh #生成dh密钥
./easyrsa build-server-full server nopass #签名请求,生成服务器证书,不需要密码
./easyrsa build-client-full client1 nopass #生成了一个名为"client1"的客户端证书,不需要密码
./easyrsa build-client-full client2 nopass #生成了一个名为"client2"的客户端证书,不需要密码
EASYRSA_CRL_DAYS=3650 ./easyrsa gen-crl #生成证书吊销列表(CRL),有效期为 3650 天,可以不设置,证书长期有效
openvpn --genkey --secret /etc/openvpn/ta.key #生成tls密钥,用密钥取代密码输入
#拷贝证书
cd /etc/openvpn/EasyRSA/pki
cp ca.crt /etc/openvpn
cp private/ca.key /etc/openvpn
cp dh.pem /etc/openvpn
cp issued/server.crt /etc/openvpn
cp private/server.key /etc/openvpn
cp crl.pem /etc/openvpn
3、创建openvpn服务端配置文件
rpm -ql openvpn |grep server.conf #查看当前版本
cp /usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf /etc/openvpn/
mv /etc/openvpn/server.conf /etc/openvpn/server.conf.bak
vi /etc/openvpn/server.conf #添加配置
port 1194 #端口
proto tcp #指定采用的传输协议,可以选择tcp或udp
dev tun #指定创建的通信隧道类型,可选tun或tap,一般设置为tun
sndbuf 0 #设置为0自动调整数据包发送缓冲区大小
rcvbuf 0 #设置为0自动调整数据包接收缓冲区大小
ca ca.crt #指定证书颁发机构(CA)的证书文件
cert server.crt #指定服务器的证书文件
key server.key #指定服务器的私钥文件
dh dh.pem #指定Diffie-Hellman参数文件
auth SHA512 #指定使用SHA512算法进行身份验证
tls-auth ta.key 0 #指定TLS密钥文件
topology subnet #指定虚拟网络拓扑结构为子网模式
server 10.8.0.0 255.255.255.0 #自定义虚拟网段,网段不能冲突
ifconfig-pool-persist ipp.txt #指定IP地址租约持久化文件
push "route 10.189.189.0 255.255.255.0" #vpn服务器所在的内网段,向客户端推送这条路由信息
push "redirect-gateway def1 bypass-dhcp" #重定向所有流量通过VPN,如果只访问内网,外网流量不通过vpn请注释掉此行
push "dhcp-option DNS 223.5.5.5" #dns服务器地址,必须和客户端设置相同,如果只访问内网,外网流量不通过vpn请注释掉此行
push "dhcp-option DNS 223.6.6.6" #dns服务器地址,必须和客户端设置相同,如果只访问内网,外网流量不通过vpn请注释掉此行
keepalive 10 120 #保持活动连接的时间和频率
cipher AES-256-CBC #加密算法为AES-256-CBC,必须和客户端设置相同
comp-lzo #启用数据压缩,必须和客户端设置相同
user openvpn #指定OpenVPN进程的运行用户
group openvpn #指定OpenVPN进程的运行组
persist-key #持久化密钥
persist-tun #持久化通道
status openvpn-status.log #指定状态日志文件
verb 3 #指定日志详细级别,必须和客户端设置相同
crl-verify crl.pem #指定证书吊销列表文件
client-to-client #允许客户端之间通信
max-clients 1000 #设置最大客户端连接数为1000
duplicate-cn #允许相同公共名称的客户端连接,一个账号可以多人同时登录
auth-user-pass-verify /etc/openvpn/server/user/checkpsw.sh via-env #指定验证用户名和密码的脚本
script-security 3 #指定脚本安全级别,必须和客户端设置相同
username-as-common-name #使用用户名作为公共名称
:wq! #保存退出
mkdir -p /etc/openvpn/server/user/ #创建目录
vi /etc/openvpn/server/user/checkpsw.sh #创建密码检查脚本
#!/bin/sh
###########################################################
# checkpsw.sh (C) 2004 Mathias Sundman <mathias@openvpn.se>
#
# This script will authenticate OpenVPN users against
# a plain text file. The passfile should simply contain
# one row per user with the username first followed by
# one or more space(s) or tab(s) and then the password.
PASSFILE="/etc/openvpn/server/user/psw-file"
LOG_FILE="/var/log/openvpn/password.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
###########################################################
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file "${PASSFILE}" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk '!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}' ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username="${username}", password=
"${password}"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username="${username}"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username="${username}", password=
"${password}"." >> ${LOG_FILE}
exit 1
:wq! #保存退出
chmod 700 /etc/openvpn/server/user/checkpsw.sh
chown openvpn:openvpn /etc/openvpn/server/user/checkpsw.sh
vi /etc/openvpn/server/user/psw-file #创建账号密码,前面是账号,后面是密码
client1 123456
client2 123456
:wq! #保存退出
#设置权限
chmod 600 /etc/openvpn/server/user/psw-file
chown openvpn:openvpn /etc/openvpn/server/user/psw-file
# 查看service名
rpm -ql openvpn |grep service
systemctl restart openvpn@server #重启服务
systemctl enable openvpn@server #开机启动
4、拷贝客户端证书
从server上将生成的ca.crt、ta.key、client1.crt、client1.key、client2.crt、client2.key、文件下载到客户端
cp /etc/openvpn/ca.crt /etc/openvpn/client
cp /etc/openvpn/ta.key /etc/openvpn/client
cp /etc/openvpn/EasyRSA/pki/issued/client1.crt /etc/openvpn/client
cp /etc/openvpn/EasyRSA/pki/issued/client2.crt /etc/openvpn/client
cp /etc/openvpn/EasyRSA/pki/private/client1.key /etc/openvpn/client
cp /etc/openvpn/EasyRSA/pki/private/client2.key /etc/openvpn/client
5、编辑,把证书合并到一个文件里面
<ca>
ca.crt里面的内容
</ca>
<cert>
client1.crt里面的内容
</cert>
<key>
client1.key里面的内容
</key>
<tls-auth>
ta.key里面的内容
</tls-auth>
cd /etc/openvpn/client
vi /etc/openvpn/client/client1.ovpn #编辑,把证书合并到这个文件
client #指定配置文件为客户端配置
dev tun #指定使用TUN设备作为通信隧道类型
auth-user-pass #指定要求用户通过用户名和密码进行身份验证
proto tcp #指定使用TCP协议传输数据
sndbuf 0 #和服务端配置一样
rcvbuf 0 #和服务端配置一样
remote 10.189.189.197 1194 #指定连接服务器的IP地址和端口号
resolv-retry infinite #在连接失败时无限重试
nobind #不绑定到特定本地地址和端口
persist-key #和服务端配置一样
persist-tun #和服务端配置一样
remote-cert-tls server #开启证书登录
push "dhcp-option DNS 223.5.5.5" #和服务端配置一样,向客户端推送DNS服务器地址,如果只访问内网,外网流量不通过vpn请注释掉此行
push "dhcp-option DNS 223.5.6.6" #和服务端配置一样,向客户端推送DNS服务器地址,如果只访问内网,外网流量不通过vpn请注释掉此行
auth SHA512 #和服务端配置一样
cipher AES-256-CBC #和服务端配置一样
comp-lzo #和服务端配置一样
setenv opt block-outside-dns #阻止客户端使用除VPN外的DNS,科学上网有用,只访问内网需要注释掉此行
key-direction 1
verb 3
<ca>
-----BEGIN CERTIFICATE-----
MIIDKzCCAhOgAwIBAgIJAKqUKgImWthIMA0GCSqGSIb3DQEBCwUAMBMxETAPBgNV
BAMMCENoYW5nZU1lMB4XDTI0MDMyNjA4MjkwNVoXDTM0MDMyNDA4MjkwNVowEzER
MA8GA1UEAwwIQ2hhbmdlTWUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB
AQDMWdwtgtLkAHsRSg13rHMdrXbEyYMIGX+45XJcV4uByqEYEQetjDVyFjPh5Lqh
3W6+vqUUreZK3LXvLr+P+STznFKlIy6wKAlpZnSCh6QxziDHE6Fkg68T/sjDC4ar
/aEEujYjAXUAqZmjksZq4L+wR3pGyJg6SslaxP9vrfEnQ1fhll//LQbaEDLYdywh
/Ay+lJkVLP5Yv5n/XIDtBF/+eDT92aMGKQWHVGth1+zSIOnnkGs9qO2RJTLESpu4
K/HKCPZkSbnwYx8JiiGj6Mcs1Li7WlFt1jQ782iYq41xgnyJi7vCW9XGAY4ZiDjQ
7DVuU1Xjvij2+bfOZjquEGX1AgMBAAGjgYEwfzAdBgNVHQ4EFgQUSQ4+53IfKl9e
kaisR1vgfmeQd6YwQwYDVR0jBDwwOoAUSQ4+53IfKl9ekaisR1vgfmeQd6ahF6QV
MBMxETAPBgNVBAMMCENoYW5nZU1lggkAqpQqAiZa2EgwDAYDVR0TBAUwAwEB/zAL
BgNVHQ8EBAMCAQYwDQYJKoZIhvcNAQELBQADggEBAEuNnIeQbCTLfLYVyfeD9lKG
JK0mer/TKsnoo5iEnXbER+HnLfQbKh3vYiD22lSJwwkZiRj/Qzy14fspRUYtM21H
Kv32LzvJLiemccGAl3uh01OMXLlNLhL/jwUNxGOe7xG63khb/gnpb0C1cte+l1/F
3VfzgrtlTyxVwPiXOO0H9JBIEeQ7YmI6w5Qk9TCVZsFo78rUQ6fGtK5Oc8g493Xu
AuBuogSfKFK+87vWL5etEF0xeGo5KRz2oGp0/0IcTvafZ/+llsgzIQU+wbIaw/CK
P5o3cXsEup+ZPN85be3lF+sb6N8Jem7a138C4e7joJIz0Fo4uHCnsZ5Vnj43Ffc=
-----END CERTIFICATE-----
</ca>
<cert>
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
9a:d9:7b:d8:5f:11:ae:b2:a8:39:00:16:a8:2c:4d:49
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=ChangeMe
Validity
Not Before: Mar 26 08:30:31 2024 GMT
Not After : Jun 29 08:30:31 2026 GMT
Subject: CN=client1
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:e8:d7:63:55:5a:83:14:4f:03:0f:21:80:d3:cd:
4e:45:68:73:91:9b:7b:96:b3:33:53:ec:24:ae:90:
a6:61:60:0f:4b:50:d0:39:47:b9:9e:0f:be:c1:5b:
06:5e:6e:fd:9d:d0:71:31:ae:5f:97:06:d3:51:c6:
61:3d:d6:ec:14:10:80:92:cd:8f:0a:75:f2:97:dc:
0f:fb:8c:6c:37:16:d9:a0:79:3e:93:3f:5e:4e:40:
1c:a8:7b:77:9f:be:34:23:9b:e5:18:67:36:4c:1e:
8e:4a:17:6c:76:21:0c:ce:6a:46:cc:3d:dd:79:ae:
a5:64:43:66:20:ee:69:00:e5:bf:2a:3b:ac:a6:e1:
f3:58:5a:2d:fb:c7:4d:dd:bc:56:65:c5:bd:6a:74:
11:47:16:1f:0f:fd:7d:ad:50:ec:30:70:eb:93:d5:
25:81:f7:ab:70:cb:41:83:ca:76:f8:40:07:e8:e0:
a2:a5:57:d4:a3:25:35:85:44:f0:81:e0:d6:2a:1f:
1c:b5:f5:11:7f:6f:ef:ab:87:89:d2:82:a6:c9:6e:
16:4f:11:aa:89:71:8d:42:73:75:55:34:2b:b2:93:
d3:de:91:ff:03:83:f8:af:f5:b3:5f:7f:36:09:f6:
08:d8:6c:4c:36:0f:e6:90:8c:db:fd:15:2b:55:6c:
e4:27
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
79:0E:78:BF:94:BA:5E:4E:DB:66:53:37:78:54:DD:93:2F:CE:22:8C
X509v3 Authority Key Identifier:
keyid:49:0E:3E:E7:72:1F:2A:5F:5E:91:A8:AC:47:5B:E0:7E:67:90:77:A6
DirName:/CN=ChangeMe
serial:AA:94:2A:02:26:5A:D8:48
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature
Signature Algorithm: sha256WithRSAEncryption
b0:b5:d6:fc:6f:07:29:f3:d3:e6:d4:77:77:d6:e3:79:8b:88:
c2:22:c6:2b:00:9a:c2:ef:39:bc:5e:0e:65:82:da:16:79:d3:
40:38:9d:51:88:2d:8d:e5:dc:33:f1:fb:dc:b2:03:d3:a0:9d:
57:22:79:73:fe:13:2a:4d:f8:b5:0f:56:a8:38:64:5e:6e:90:
88:64:29:fa:9c:54:1c:02:73:4a:10:69:f2:1d:8c:90:de:2e:
9c:88:b8:8c:ce:88:a3:54:38:23:19:63:e8:4e:14:ab:56:b0:
3c:e8:71:a1:88:a1:06:3b:d1:b0:56:56:43:cc:5c:b1:88:73:
32:a6:7c:77:04:35:19:68:75:b7:90:7f:65:f9:3e:93:5a:ad:
4e:38:b1:14:5b:50:07:08:37:25:f8:d7:ac:06:83:1a:b3:ea:
5b:c4:26:15:10:11:cf:be:75:52:1d:b7:35:06:98:fc:5b:dd:
53:4f:5a:de:e0:4a:91:81:85:a8:bf:fe:3a:11:42:b4:58:5f:
84:96:5b:3e:af:55:d5:e9:08:6a:9d:7f:25:f8:70:1f:7b:56:
ce:52:2a:07:37:c8:55:d8:b5:a9:c4:46:7a:fe:50:69:ff:37:
5e:f9:19:4c:eb:ce:90:9e:d4:ea:9d:52:36:26:22:6f:ca:f4:
c4:d1:51:ce
-----BEGIN CERTIFICATE-----
MIIDRTCCAi2gAwIBAgIRAJrZe9hfEa6yqDkAFqgsTUkwDQYJKoZIhvcNAQELBQAw
EzERMA8GA1UEAwwIQ2hhbmdlTWUwHhcNMjQwMzI2MDgzMDMxWhcNMjYwNjI5MDgz
MDMxWjASMRAwDgYDVQQDDAdjbGllbnQxMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
MIIBCgKCAQEA6NdjVVqDFE8DDyGA081ORWhzkZt7lrMzU+wkrpCmYWAPS1DQOUe5
ng++wVsGXm79ndBxMa5flwbTUcZhPdbsFBCAks2PCnXyl9wP+4xsNxbZoHk+kz9e
TkAcqHt3n740I5vlGGc2TB6OShdsdiEMzmpGzD3dea6lZENmIO5pAOW/KjuspuHz
WFot+8dN3bxWZcW9anQRRxYfD/19rVDsMHDrk9UlgfercMtBg8p2+EAH6OCipVfU
oyU1hUTwgeDWKh8ctfURf2/vq4eJ0oKmyW4WTxGqiXGNQnN1VTQrspPT3pH/A4P4
r/WzX382CfYI2GxMNg/mkIzb/RUrVWzkJwIDAQABo4GUMIGRMAkGA1UdEwQCMAAw
HQYDVR0OBBYEFHkOeL+Uul5O22ZTN3hU3ZMvziKMMEMGA1UdIwQ8MDqAFEkOPudy
HypfXpGorEdb4H5nkHemoRekFTATMREwDwYDVQQDDAhDaGFuZ2VNZYIJAKqUKgIm
WthIMBMGA1UdJQQMMAoGCCsGAQUFBwMCMAsGA1UdDwQEAwIHgDANBgkqhkiG9w0B
AQsFAAOCAQEAsLXW/G8HKfPT5tR3d9bjeYuIwiLGKwCawu85vF4OZYLaFnnTQDid
UYgtjeXcM/H73LID06CdVyJ5c/4TKk34tQ9WqDhkXm6QiGQp+pxUHAJzShBp8h2M
kN4unIi4jM6Io1Q4Ixlj6E4Uq1awPOhxoYihBjvRsFZWQ8xcsYhzMqZ8dwQ1GWh1
t5B/Zfk+k1qtTjixFFtQBwg3JfjXrAaDGrPqW8QmFRARz751Uh23NQaY/FvdU09a
3uBKkYGFqL/+OhFCtFhfhJZbPq9V1ekIap1/JfhwH3tWzlIqBzfIVdi1qcRGev5Q
af83XvkZTOvOkJ7U6p1SNiYib8r0xNFRzg==
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDo12NVWoMUTwMP
IYDTzU5FaHORm3uWszNT7CSukKZhYA9LUNA5R7meD77BWwZebv2d0HExrl+XBtNR
xmE91uwUEICSzY8KdfKX3A/7jGw3FtmgeT6TP15OQByoe3efvjQjm+UYZzZMHo5K
F2x2IQzOakbMPd15rqVkQ2Yg7mkA5b8qO6ym4fNYWi37x03dvFZlxb1qdBFHFh8P
/X2tUOwwcOuT1SWB96twy0GDynb4QAfo4KKlV9SjJTWFRPCB4NYqHxy19RF/b++r
h4nSgqbJbhZPEaqJcY1Cc3VVNCuyk9Pekf8Dg/iv9bNffzYJ9gjYbEw2D+aQjNv9
FStVbOQnAgMBAAECggEAcoZ2smXZsWSHoaqd/g+unw8YQRdT+7Ta2z18cWxumdiw
zR/Lu1DfKLKf5eUKxeobzsLW2lPlapiN2lwUOmF7LwdK5mo7IC8RisZQCi9wjswr
cPYR5EU38o8wSWKpXSYl6Rnl3lHt8BTbcfABhj0NWn4ForIPPKm9agqIskvx0+E9
Ae4TzkFEAJCM7V1vWA2UX4+Wnj7+6oMd8qMEN+1PwtM+IUahTPFJQOc8PAW8tJi9
5h673xbwc+YpnDRU232KQGbto2eH6+eKVIJg50jis86aioLbAle/8272e9iSP1RP
Y8GTqH4czCpgFgs2JSDghUvj0Z1S9Snkd3xiICpRcQKBgQD9yiAYrQKMe7Wxm1J4
TeWBQsZkQPRebCvihj9T/2n4qVISpPZuO7Iuvhj7KNj2733zdiMnO39gw95NtfAn
qLKoavWFHw2BKnIA20Fw5pqnZjSSS2AlBoOQuQOb2iK/BoHt0mlIF2Mlb8Yuefzb
RoEZupdIRQz3Q9ptj+dGD3NL2QKBgQDq3o3wt2Jl0qfLKrZQ0BaFfQ5voWOz9Hqe
15RZ3KaOABSGCKJ7TWX9p0vTehEoZzBm2B5c2OtZea6gsnrC3JuoIuqdQ996ASXg
rU8VhGduDKReQj80cvwSmvcCdhicaQ25OWEUzu+6OWr+CyJu9uUUzm2M4DSrQF1h
AIW92LOv/wKBgG5Iql/utr/TdmZCp7jNqODd4pZoP4jUmtFqIxTeVe+PrLGba9cF
K+3x/6sM2hOciPAGM0p2KWkkVHMSj9S8Ez7qk9yQXO73QekrXimwnB4IZOn5xULx
rLR0IaRVS2oVatqs58FDIHuBMe66Ze3nmmxS0DDAiNzeaInZ0dd5GVIpAoGBAJHr
lYohlUuntkH+lmjc77EdwjNOtNAgK3K2g1/VO9FrcVTY1oH+00flgbGw3Coa+jJb
QXnz9zyO4hTK7oRUZYzvrI3qllSJlAvkAQdgTJZN2m0JgZVHfx7cEm0ADEhY6ILU
iGFSNBSiCbwuFMWWNTtZCS0GOxLOmXVjyrPph7HnAoGBAIF3udcuSAQusciA2ASy
MSBRMkJMVIxANWDgvMdOdTGWRbXA/IlKwyLDFXgZoQK/YGiLmWUaz50cy8hAJBL7
TOlL8arJzruVgnrjqhj3WDBZvogx05k3J85PRQ8dDad9BMCPWmFn+I5jGWv8rgVB
NpRp9zvWjwELAiOqQpUPfZa5
-----END PRIVATE KEY-----
</key>
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
d2db59c6690bb3f05ce331fc66464f9f
5382329a16b515ebe402ae1458a97673
c160507123c76373f7be093b200ab838
9309113dafa8db1d1b1b80d9f7e355d9
25a2cecaa533d74d80951a0ecf50a334
15cb9d7fe1d3c828f20e2694e46982ae
49e32e889a401ad733b10bbfbffcaa13
d39ea0e0a324bde71064e3e5e83ed3a8
d7e5921528d4b0c75db07ee2ca271009
68b6343bcc5303446320a48dd1c2cc12
1937f4c2cbb180cf261caebb20447840
be1f9591ade5ced4056958150b6e107b
a7d14fe439576b9c270ce165c1b8346f
e31b66d96c5225e052ac75cc3e62c43d
ab4ac08a0807d3c2afc426bdd1325070
bc21d96dee5123ea5a2bf7f982570c16
-----END OpenVPN Static key V1-----
</tls-auth>
:wq! #保存退出
6、设置iptables防火墙转发规则,否则登录之后无法访问网络
iptables -I FORWARD -s 10.8.0.0/24 -j ACCEPT
iptables -I FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to 10.189.189.197
iptables-save > /etc/sysconfig/iptables #保存规则
systemctl restart iptables.service #启动防火墙使配置生效
cat /etc/sysconfig/iptables #防火墙配置文件
# Generated by iptables-save v1.4.21 on Tue Mar 19 15:57:47 2024
*nat
![]() REROUTING ACCEPT [12975:2079674]
REROUTING ACCEPT [12975:2079674]
:INPUT ACCEPT [134:8032]
:OUTPUT ACCEPT [166:12426]
![]() OSTROUTING ACCEPT [167:12486]
OSTROUTING ACCEPT [167:12486]
-A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to-source 10.189.189.197
COMMIT
# Completed on Tue Mar 19 15:57:47 2024
# Generated by iptables-save v1.4.21 on Tue Mar 19 15:57:47 2024
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [108908:56620509]
-A INPUT -p tcp -m tcp --dport 1194 -j ACCEPT
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -s 10.8.0.0/24 -j ACCEPT
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
# Completed on Tue Mar 19 15:57:47 2024
7、设置目录权限
chown openvpn:openvpn /etc/openvpn/ -R #设置权限,重要,否则客户端登录不上去
systemctl restart openvpn@server #重启服务
三、测试篇
下载/etc/openvpn/client/client1.ovpn到本地客户端
Windows客户端
C:\Program Files\OpenVPN\config
放到这个目录
安装openvpn客户端
客户端下载地址::https://www.techspot.com/downloads/5182-openvpn.html
安装完成之后打开客户端导入配置文件:client1.ovpn
输入用户名密码进行连接
直接输入内网地址即可访问办公室服务器
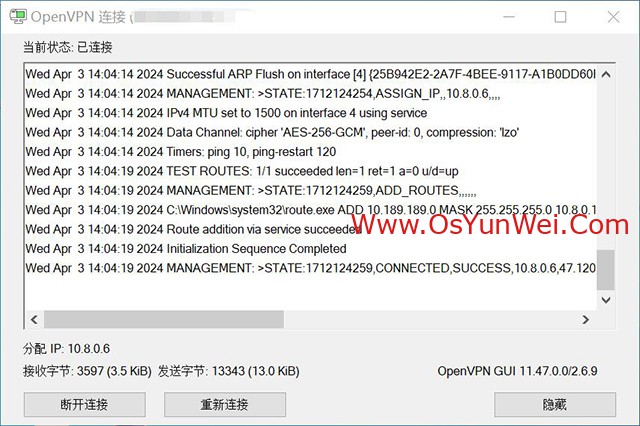
特别说明:
要实现只让特定流量通过 VPN 连接,而其他流量绕过 VPN 直接连接到互联网。
服务端配置文件只设置这个一个push,其他的push删掉
push "route 10.189.189.0 255.255.255.0" #vpn服务器所在的内网段,向客户端推送这条路由信息
客户端配置文件,删掉下面的这个参数
;setenv opt block-outside-dns #阻止客户端使用除VPN外的DNS,科学上网有用,只访问内网需要注释掉此行
至此,Linux系统安装部署Open-VPN服务器完成。

 ②190706903
②190706903  ③203744115
③203744115 







